Identify Assets for CMMC (Scoping FCI and CUI)
This blog enables contractors with the ability to identify the assets that fall into their existing IT boundaries for CMMC compliance. Step 2: identify assets for CMMC 2.0.
Identify Assets for CMMC (Scoping FCI and CUI)
When it comes to current compliance mandates for the DoD supply chain, identifying assets and data in your existing IT environment can be a challenge because of the potential areas in which contract information (FCI) and sensitive data (CUI) can flow. The goal of this blog is to enable contractors, specifically small to medium-sized contractors, with the ability to identify the assets, systems, and people that fall into their existing IT boundaries.
This blog will cover how to identify assets for CMMC Level 1 and Level 2, and then what next steps contractors should take in their security and compliance journey.
A few of the initial questions we’re going to ask to drive the asset identification conversation:
- How does data flow in and out of your current environment?
- Do you know where your FCI / CUI lives, or could potentially live?
- Do you have control over the systems holding contract information/sensitive data?
Here’s the problem: many contractors in the Defense Industrial Base understand that asset identification is needed for CMMC preparation, but why is it so challenging? A few suggested reasons:
- The complex burden of shifting an entire organization to maintain a strong cybersecurity posture
- Most companies don't have the resources to dedicate to building and maintaining this process
- Clearly identifying markings, distribution statements, etc. is not common knowledge
- The necessity of CMMC preparation as a result of moving DoD timelines
- The reoccurring impacts of cost
- Company-wide issues and users’ follow-through
- The overall lack of competency and resources to gain the skills or understanding needed
Not to mention – an extreme difficulty IT administrators might have when it comes to convincing their leadership team that pursuing CMMC compliance should not wait.
CMMC Scoping Guidance
DOD's Level 1 Scoping Guidance Before a Level 1 Cybersecurity Maturity Model Certification (CMMC ) Self-Assessment, the contractor must specify the CMMC Self-Assessment Scope. The CMMC Self-Assessment Scope informs which assets within the contractor’s environment will be assessed and the self-assessment details.
Federal Contract Information (FCI) Assets process, store, or transmit FCI as follows:
- Process – FCI can be used by an asset (e.g., accessed, entered, edited, generated, manipulated, or printed).
- Store – FCI is inactive or at rest on an asset (e.g., located on electronic media, in system component memory, or in a physical format such as paper documents).
- Transmit – FCI is being transferred from one asset to another asset (e.g., data in transit using physical or digital transport methods). FCI Assets are part of the CMMC Self-Assessment Scope and are assessed against applicable CMMC practices.
Federal Contract Information (FCI) assets that process, store, or transmit FCI fall into the CMMC Level 1, or self-assessment, category with the appropriate 17 controls under CMMC Level 1.
Some examples of FCI would be contract performance reports, organizational or programmatic charts, process documentation, etc. These are most likely provided by the Government, but some can originate from your people. Additional guidance on CMMC Level 1 can be found in the DoD's scoping guide for Level 1.
DOD's Level 2 Scoping Guidance
Before a CMMC Level 2 third-party assessment, the contractor must specify where Controlled Unclassified Information (CUI) falls in the Level 2 asset categories below defined by DoD’s scoping guidance.
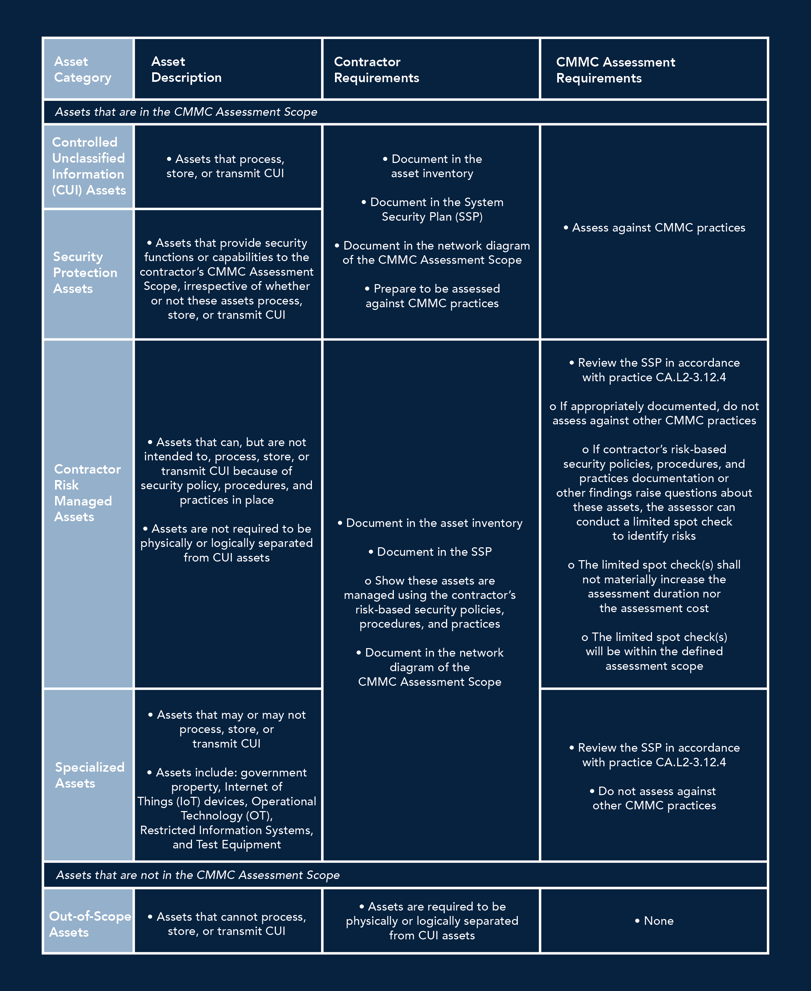
CMMC Asset Category Table for Level 2
As a reminder from the previous blog, CMMC Level 2 requires organizations to satisfy 110 practices that directly align with NIST SP 800-171. Scoping guidance clearly states that the contractor is required to document all assets as well as classify them into 4 categories.
Identifying and Defining Assets For CMMC Level 2
There are four primary types of assets as well as “Out of Scope” assets that make up the guidance for CMMC Level 2: - CUI Assets
- Security Protection Assets (SPA)
- Contractor Risk Managed Assets (CRMA)
- Specialized Assets (SA)
- Out-of-Scope Assets
CUI Assets
Controlled Unclassified Information (CUI) assets are assets that process, store, or identify CUI.
Controlled Unclassified Information assets are essential to the success of a DIB organization in its support of the DoD, so identifying these assets should be at the top of the list when it comes to not only compliance but healthy cybersecurity practice as a whole. Organizations should clearly define the workstations, file servers, cloud collaboration services, and/or managed service providers.
Here’s an easy way to remember CUI: 
C – Is the data Created on behalf of a contract, or distributed directly from the prime or DoD?
U - Is the data going to be Used to deliver your contractual responsibilities to the government?
I - Can the data type be Identified within the sub-categories listed on the NARA CUI registry?
Ask yourself: Have we identified our current CUI boundaries and built network diagrams?

Note: new contract award, organic company growth, acquisition activity, or anything that creates additional complexities could intensify the need for diligent data management and asset classification.
The reality of getting the support needed to tackle overwhelming IT projects, or the award of new DoD contracts, drives the need for applications such as productivity suites, Enterprise Resource Planning (ERP) software, and file collaboration. The increase in technical burden from these additions could lead companies to utilize a compliant Managed Service Provider (MSP) or Managed Security Service Provider (MSSP) who is required to have a shared responsibility matrix.

Here’s the problem: the aforementioned items have access to your sensitive data, forcing companies to forsake the use of the software or service providers unless a clear boundary has been defined and documented.
1. Can you show me your Shared Responsibility Matrix and how it maps to CMMC / NIST 800-171A?
2. Is your application FedRAMP Moderate equivalent or higher?
-
-
FedRAMP Compliance for Partners: Since 2016 DFARS clause 252.204-7012 has said that if a contractor puts CUI in the cloud then the contractor needs to require and ensure that the cloud service provider meets security requirements "equivalent" to the FedRAMP Moderate baseline.
On 12/21/23, the DoD released a memo clarifying the stringent requirements of FedRAMP moderate “equivalency”– and it’s effective immediately. DoD Contractors are now on the hook for their Cloud Service Provider’s (CSP) FedRAMP compliance. According to the memo: the DoD requires a lot of contractors with defense data being stored, processed, or transmitted with a FedRAMP Equivalent CSP.
A FedRAMP Moderate Authorized CSP will require considerably less effort by the contractor. You can check if your CSP is Authorized on the FedRAMP marketplace. If you do have an FedRAMP moderate "equivalent” CSP, you might consider switching to a FedRAMP-Tailored Solution. We recommend either Microsoft GCC or GCC High.
3. Are you clear on the responsibility you might have when it comes to the protection of my data? -
CUI assets will be assessed against CMMC practices at Level 2, like Security Protection Assets.
Security Protection Assets (SPA)
Security Protection Assets are assets that provide security functions or capabilities to the contractor’s CMMC Assessment Scope, irrespective of whether or not these assets process, store or transmit CUI.
Notice the language that the DoD uses when it comes to SPAs – irrespective. If your company maintains firewalls, switches, spam filters, protection for endpoints, or leverages an external provider for these functions, then it will fall into the SPA asset category.
There are plenty of applications and interfaces that can achieve desired outcomes, but they all come with associated risk. Many organizations in the DIB choose to rely on Microsoft products to achieve the desired outcomes for protection mechanisms because of Microsoft’s ability to provide a single platform for collaboration, security, and compliance.
Contractor Risk Managed Assets (CRMA)
Contractor Risk Managed Assets are assets that can, but are not intended to, process, store, or transmit CUI because of security policy, procedures, and practices in place. CRMAs are not required to be physically or logically separated from CUI assets.
CRMAs can include things like devices connecting to secured virtual desktop instances (VDIs), systems that do not house CUI as a result of technical controls or policies, or any secure enclave defined in a scoping boundary. There is much debate in the CMMC ecosystem about whether the right approach to CMMC is via a secure enclave such as Azure Virtual Desktop or not; organizations should not necessarily be asking if an enclave is the right approach but should consider taking a step back to identify and assess precisely where their CUI lives, and where it could potentially flow.
By partitioning off company and personal devices via a remote desktop application, companies can control the flow of CUI in their efforts to maintain compliance.
Specialized Assets (SA)
Specialized Assets are assets that may or may not process, store, or transmit CUI. These assets include government property, IoT devices, operational technology (OT), restricted information systems, and test equipment.To reiterate: manufacturing systems, IoT devices, operational technology, restricted information systems, and test equipment are deemed “in scope", but they are not assessed against the 110 practices. Translation – contractors are able to save a significant amount of money because manufacturing systems won't be on the test.
Note: these still have to be documented in the asset inventory, SSP, Network Diagram, and an assessment report (risk management).
Out of Scope Assets
Out of Scope assets are assets that cannot process, store, or transmit CUI.
The good news for contractors is that these are not assessed under CMMC , and do not have to be documented in SSPs for CMMC . Anything that does not or will not house CUI in your existing environment would fall into this category.
Think personal employee information assets such as LinkedIn or documents that are not sensitive to the nature of your business.
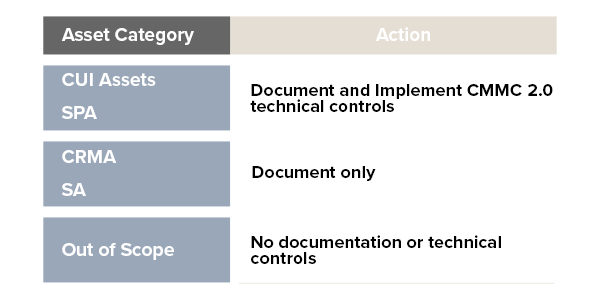
CMMC Level 2 Asset Categories and Action
How to Identify Assets for CMMC Compliance
The most important thing to remember when discussing Out of Scope assets, and the other four categories in the Level 2 scoping guide for that matter, is that it is critical that you inventory your systems, people, data flow and assign them to their respective areas or buckets. This step will save organizations a significant amount of time and energy preparing for a CMMC assessment.
Many small to medium-sized businesses in the DIB are relying on Microsoft’s suite of security products to prepare for CMMC Level 1 and CMMC Level 2, specifically Microsoft Purview, to identify assets for CMMC compliance.
Microsoft Purview holds a feature called “Content search” that is not only beneficial to contractors trying to identify their data landscape and assessment scope, but it can also validate their data flow control capabilities already implemented.
As previously mentioned, for a company to identify its assets for CMMC compliance, it must first understand its defined level of CMMC . In the next blog, we'll cover how to choose your technical design for CMMC.
To follow along in this 7-part blog series: The 7 Steps to CMMC Compliance, subscribe to the Summit 7 blog and be sure to subscribe to the Summit 7 YouTube channel to get notified of supporting content. Click the image below to read the next blog in the series.