Microsoft Defender in Microsoft 365 GCC and GCC High
Recently, Microsoft consolidated several of its security products into the Microsoft Defender suite as a wholistic Extended Detection and Response (XDR) Strategy for Office 365 GCC High and Microsoft 365 GCC High. This consolidation was announced in late 2020.
Recently, Microsoft consolidated several of its security products into the Microsoft Defender suite as a wholistic Extended Detection and Response (XDR) Strategy for Office 365 GCC High and Microsoft 365 GCC High. This consolidation was announced in late 2020 along with the following name changes to better align nomenclature. Microsoft Threat Protection has become Microsoft 365 Defender, Azure Advanced Threat Protection is now known as Microsoft Defender for Identity, and Microsoft Defender Advanced Threat Protection is Microsoft Defender for Office 365.
Each of these new name changes signifies further alignment of Microsoft’s security products under the Microsoft Defender suite. This allows each of the products to share threat signals to administrators so they can see the full scope and impact of each threat across the data estate, including locations where Controlled Unclassified Information (CUI) may reside. Each component of the Microsoft Defender suite works together to create a fully integrated security solution for DoD contractors. These changes will be reflected in Azure, Microsoft 365 Commercial, GCC and GCC High. Below is a description of the functionality of each, and its potential to impact those seeking to attain or maintain compliance with the Cybersecurity Maturity Model Certification (CMMC), especially Level 3.
Components of Microsoft Defender
Microsoft Defender for Endpoint is a unified endpoint platform for preventative protection, post-breach detection, automated investigation (available in Commercial and GCC only), and response. It provides advanced attack detections that are near real-time and actionable, allowing security analysts to gain visibility into the full scope of the breach.
As part of Microsoft's commitment to a growing need for increased vigilance in regards to cybersecurity, they have worked to make Defender for Endpoint available in both GCC and GCC High. However, it's important to note that while both GCC and GCC High meet FedRAMP High standards, Microsoft 365 GCC High is built on Azure Government rather than Azure Commercial, so only US persons access data during administrative functions, which allows DIB suppliers the ability to manage alerts in a cloud environment suitable for CUI and ITAR data.
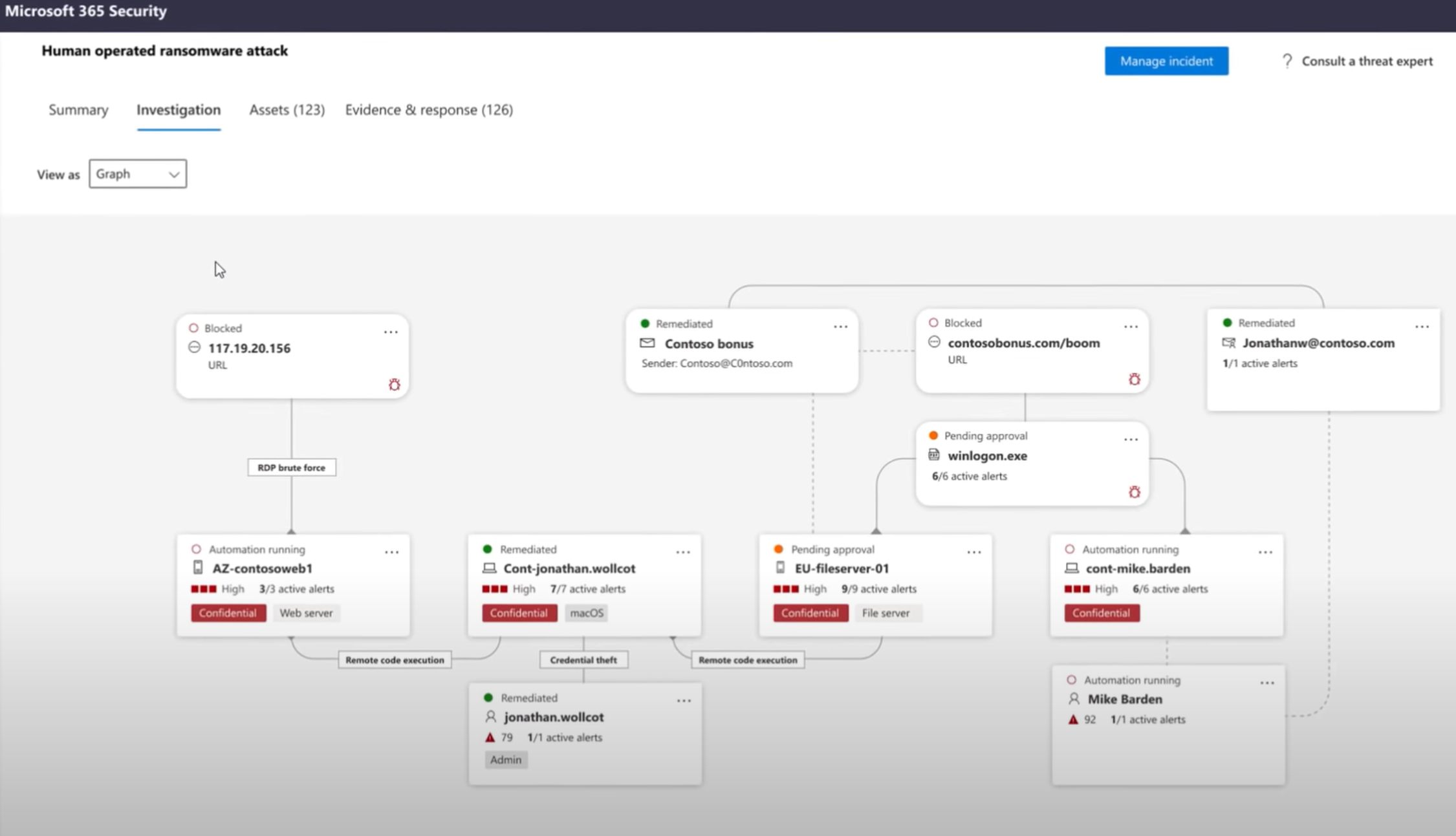
When a threat is detected, alerts are created in the system for investigation. Alerts with the same attack techniques or attributed to the same attacker are aggregated into an entity called an incident. Defender continuously collects behavioral cyber telemetry, and this includes process information, network activities, deep optics into the kernel and memory manager, user login activities, registry and file system changes, and others. This information is stored for six months, creating records that allow analysts to trace all malicious activities back to the beginning of an attack.
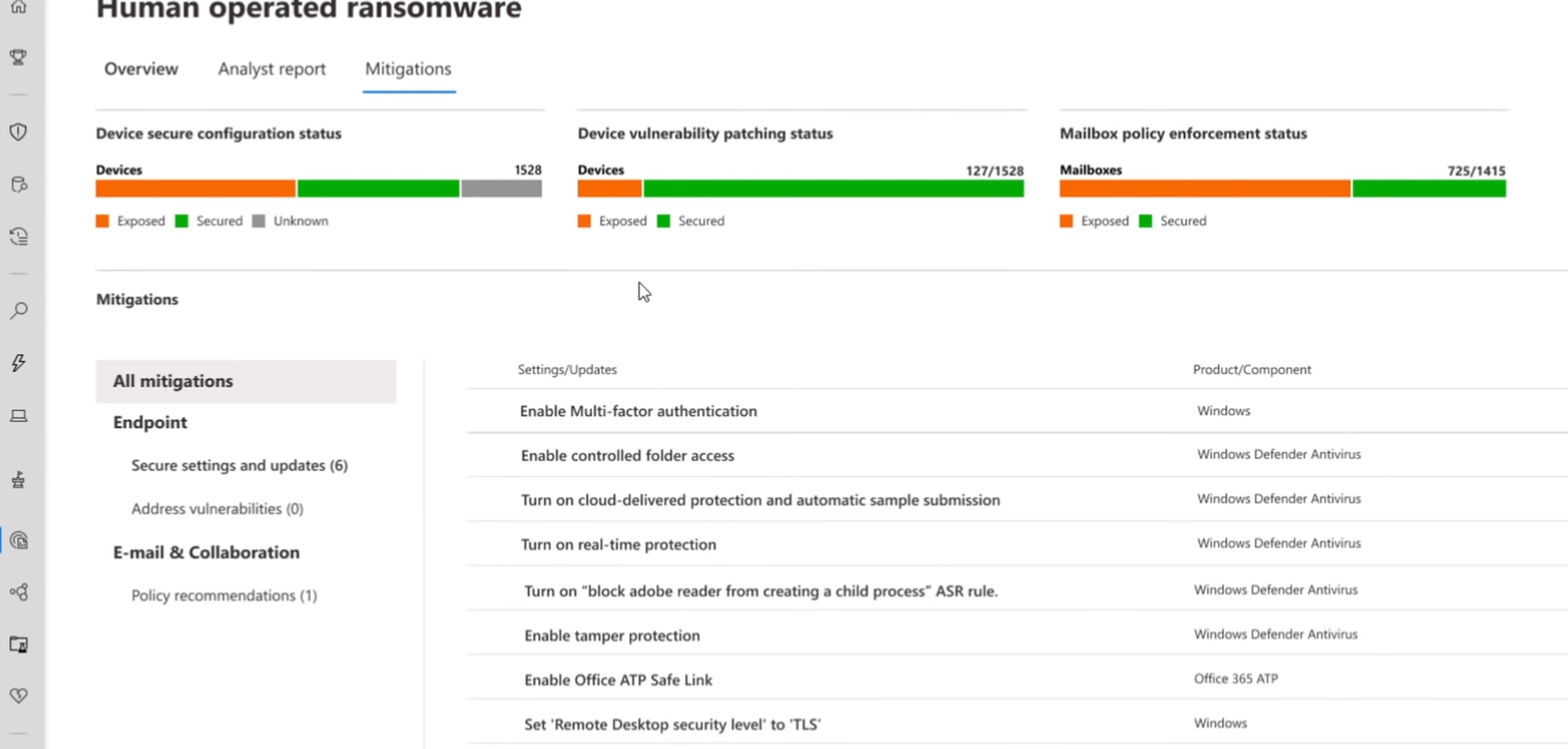
These capabilities impact compliance in multiple CMMC domains: Access Control, Audit and Accountability, Incident Response, Security Assessment, and System & Information Integrity.
Licenses – Included in Microsoft 365 E5, or Windows 10 E5 as a standalone license. The greatest feature parity gaps are in the analytics, reporting, and integration capabilities.
Microsoft Defender for Identity uses Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organizations. Defender for Identity monitors and analyzes user activities and information across your network, such as permissions and group membership, creating a behavioral baseline for each user that is then used to identify anomalies using built-in AI. These insights into suspicious activities can reveal advanced threats, compromised users, insider threats. Defender for Identity also provides security reports and analytics to help quickly identify and assess paths of attack inside your organization.
Features that are released for Microsoft Defender for Identity, should be available in GCC High within three weeks of release in the Defender for Identity commercial environment; however, we always recommend slower rollouts across your enterprise, as many features may start as Preview at first. Preview features may not be supported in the GCC High environment
Aerospace and Defense companies can attain to or maintain CMMC compliance in the Access Control, Audit and Accountability, Incident Response, and Risk Management, Situational Awareness, and System and Information Integrity domains in part with the proper configuration and management.
Licenses - Included in licensing for Enterprise Mobility + Security E5, Microsoft 365 E5. Not available as a standalone license in GCC High. MS Defender for Identity does not fully integrate with MS Defender for Endpoints as of this writing; however, it is highly important on Microsoft's roadmap.
Microsoft Defender for Office 365 safeguards your organization against malicious threats posed by email messages, links (URLs) and collaboration tools. It includes threat-detection policies, reporting, threat investigation and response capabilities, and automated investigation and response capabilities. Defender for Office allows you to configure Safe Attachment and Safe Links policies in Outlook, advanced threat protection for interoffice collaborative tools like SharePoint, OneDrive and Microsoft Teams, and anti-phishing protection. Reports update in real-time, providing recommendations and alerts to imminent threats.
The reporting and threat-detection can help organizations seeking to fully comply with the Access Control and Audits & Accountability CMMC domains, specifically the Access Control practices in levels three, four and five.
Licenses – Included in Microsoft 365 E5, Office 365 E5. Can be added to Office 365 Enterprise F3, E3, and E1 licenses.
Microsoft Cloud App Security (MCAS) is a comprehensive cross-SaaS solution bringing deep visibility, strong data controls, and enhanced threat protection to your cloud apps. It provides visibility and control over data traffic, and analytics to detect and mitigate cyberthreats across all cloud services. Natively integrating with Microsoft solutions, it deploys simply, providing centralized management and automation capabilities for key processes. Cloud App Security provides granular visibility into and control over user activities and sensitive data, preventing shadow IT attacks from unauthorized apps and devices.
Many of the policies available from this service allow contractors to comply with the practices in the Access Control, Audit & Accountability, Identification & Authentication, Risk Management, Security Assessment, and System & Information Integrity domains.
Licenses – Included in Microsoft 365 E5 and EM+S E5, or it can be purchased as a standalone license.
Examples of Microsoft Defender Meeting CMMC
As mentioned, the new Defender suite alignment is also available in GCC and GCC High and it provides controls, policies, and tools needed for contractors who are looking to be assessed for CMMC. Below are some of the practices that can be met in part by using the capabilities and features of the fully integrated Defender suite.
AU.2.044: Review audit logs. AND
AU.3.048: Collect audit information (e.g., logs) into one or more central repositories.
These two practices are both focused on keeping accurate, easily accessible audit logs. Storing audit logs in a centralized location and reviewing them regularly increases the organization’s situational awareness and protects audit logs from incidental damage or loss. This also supports automated analysis capabilities including the correlation of events across the organization. Microsoft Defender automatically creates and stores logs of different user activities. Azure Sentinel can also ingest these signals and other non-Microsoft endpoints for a complete outlook to meet AU.2.044 and 3.048.
Each of the components in the Microsoft Defender suite use integration and automation to create records of user activities, flagged according to threat level. This provides visibility to security analysts as they work to review any possible breaches of CUI and for organizations looking to gain compliance with CMMC practices.
SI.1.211: Provide protection from malicious code at appropriate locations within organizational information systems.
Microsoft Defender for Endpoint has endpoint detection and response capabilities that can be deployed to intelligently respond to advanced threats that may have otherwise gone unchecked. Microsoft Defender for Office 365 helps protect your organization against unknown malware and viruses by providing zero-day protection and safeguarding your organization from potentially malicious links. It also includes reporting and URL trace capabilities to help give administrators insight into other attack forms.
RM.2.142: Scan for vulnerabilities in organizational systems and applications periodically and when new vulnerabilities affecting those systems and applications are identified.
Defender for Identity offers an attack timeline view and smart analytics to efficiently investigate threats, and gain insights across the organization's identity data, device behavior and activity, and network traffic. This along, with correlations between Microsoft Defender for Endpoint provides additional detection and protection against advanced persistent threats coming through multiple vectors.
Microsoft Defender for Endpoint also can reduce the volume of alerts through rules and playbooks to enable incident response for smaller teams within most small to midsize DoD suppliers. Though no official date has been set by Microsoft, eventually Defender in GCC High will provide a managed threat hunting service that provides proactive hunting, prioritization, and insight collection to identify and respond to new threats before a compromise can occur.
AC.2.013: Monitor and control remote access sessions.
This practice covers a wide array of 'remote sessions' and encompasses access to cloud applications from multiple endpoints. To assist in meeting this aim, Microsoft Cloud App Security is designed to help administrators and users alike understand, classify, and protect the exposure of sensitive information at rest. With custom policies and processes, organizations can apply controls in real-time across all cloud apps, protecting against cyberthreats and anomalies.
Consolidation with a Purpose
Microsoft's decision to consolidate its security products and ensure integration between them creates additional benefits for contractors and organizations in the DIB. These once disparately named products geared towards protecting specific attack areas are now following a cohesive naming convention to be more easily recognized and managed from a licensing stand point. The integration of each of the products ensures that, when used together, organizations gain increased visibility, an extra layer of security, and automated processes geared around recording, analyzing and predicting vulnerabilities by incorporating machine learning and AI. Having integrated native security tools within the platform can also make CMMC compliance and assessments less challenging or complex by limiting the number of products to maintain.
Azure Sentinel is another tool in the arsenal of threat detection, analysis, and incident response that many organizations use to collect all signals in a central repository for CMMC/DFARS compliance. Read about its feature set and application here.