Why DoD Rulemaking and Timelines Are Driving The Security Posture of the DIB
The DoD continues to establish rulemaking for the handling of critical data specific to suppliers in the DoD. This blog gives contractors the information needed to take next steps.
The Department of Defense (DoD) has spent multiple months reviewing and updating existing policy for handling Controlled Unclassified Informed (CUI), as well as updating other federal regulations for contractors in the Defense Industrial Base. With the release of CMMC 2.0 in late 2021, the rulemaking landscape for 2022 is becoming clearer for those preparing for upcoming assessments of their I.T. environments. This is critical because aerospace and defense contractors in the DoD supply chain are afforded the ability to answer questions such as should my organization spend money on CMMC 2.0 solutions before rules are established?
As rulemaking becomes final, regulations are codified in federal registers, which means that there is specific guidance for DoD suppliers and the governance of critical data. In this blog, you will find information about the proposed and final changes for 2022 under the following federal policies:
Key idea: remember that 2022 will look dramatically different than 2021. Overall, not much happened in 2021 due to the lengthy internal review of the CMMC program by the Pentagon. Additionally, GAO conducted their own analysis of the CMMC program. The output of those reviews resulted in CMMC 2.0, released in November of 2021.
Now that the calibration of the CMMC program is complete, the DoD’s “Strategic Intent” is free to move through rulemaking and ultimately end up as a contract clause for DoD suppliers.
.png?width=773&name=MicrosoftTeams-image%20(28).png)
FAR
-
The FAR CUI rule is the missing piece of the three-part, government-wide CUI program:
-
-
32 Code of Federal Regulations section 2002 implements the CUI program for all executive branch agencies by codifying Executive Order 13556 signed by President Obama in 2010.
-
NIST SP 800-171 standardizes the minimum baseline of security controls for Controlled Unclassified Information across all agencies.
-
The FAR CUI rule will create a common mechanism (a contract clause) to communicate which information must be protected that contractors create for and receive from the Federal Government, how to protect that information, and with whom that information can be shared.
-
-
The FAR CUI rule has been anticipated since 2016, and due to this delay, marked and/or identified CUI has been hard to come by.
-
However, when the FAR CUI rule is published, expect a sudden and dramatic increase in marked and/or identified CUI.
-
-
Also, recognize that NIST SP 800-171 is the minimum baseline for any category of CUI for all agencies and contractors. When the FAR CUI rule is issued, the same pain points present in the Defense Industrial Base will be exposed in other contracting domains (NASA, DHS, GSA, etc.).

DFARS
-
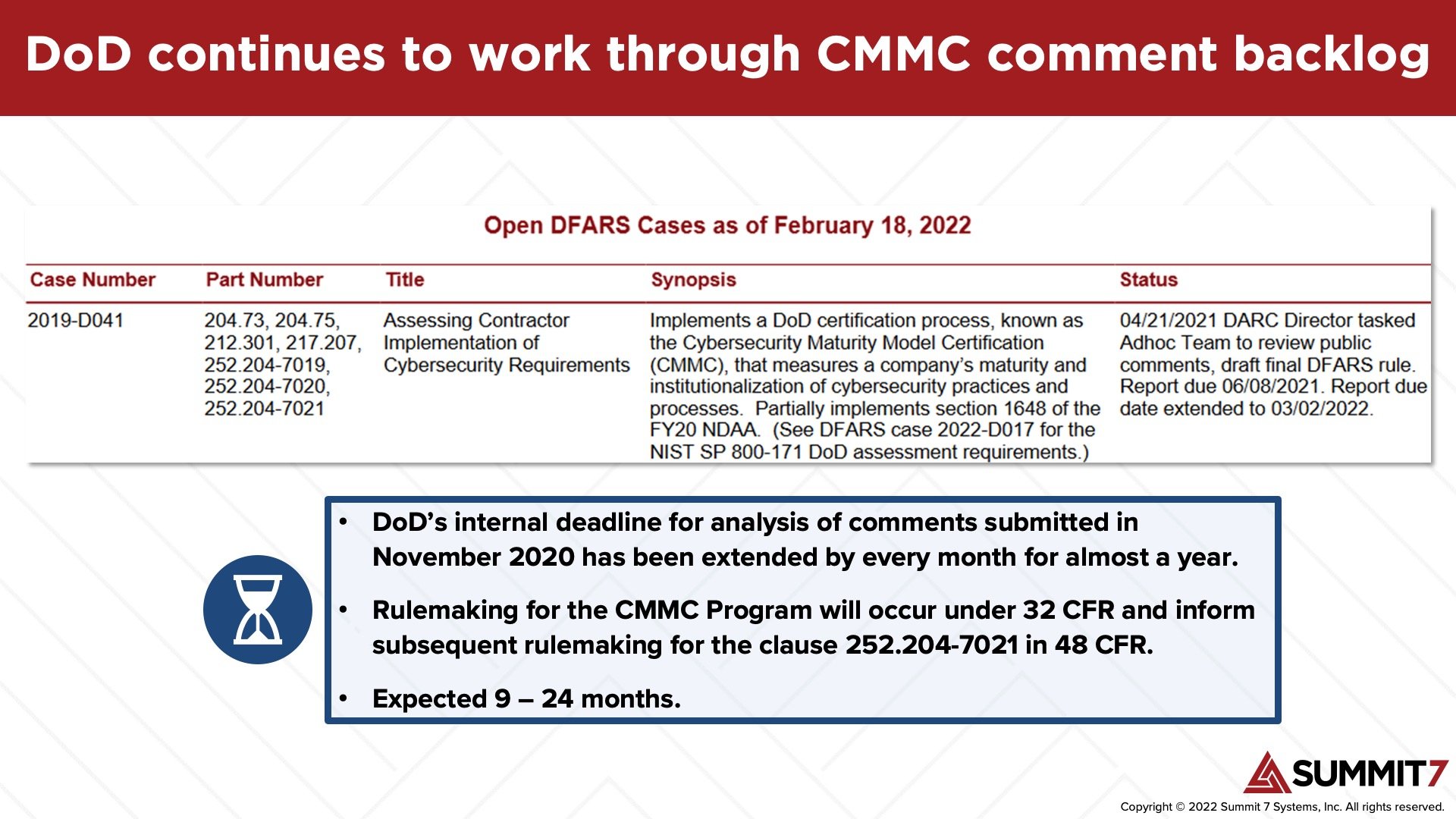
The Defense Industrial Base Cybersecurity Program (“DIB CS”) is an information and threat intelligence sharing program that is currently only open to cleared defense contractors. A small number of non-cleared defense contractors are also currently in a pilot program, in anticipation of a proposed rule that would expand access to the program to all defense contractors.
-
The DIB CS rule is currently slated for initial publication in June of 2022. Rulemaking typically takes 12 – 18 months. As a result, DoD-provided tools and services will probably not be comprehensive enough or available in time to satisfy much of the requirements in NIST SP 800-171 and CMMC.
-
The DIB CS program is often touted by the DoD as a primary tool for achieving cyber resiliency. Although the tools and services provided by the DoD DC3, DCISE, and DIB CS are useful, they have limited compliance value when compared to the requirements under NIST SP 800-171 and CMMC.
-
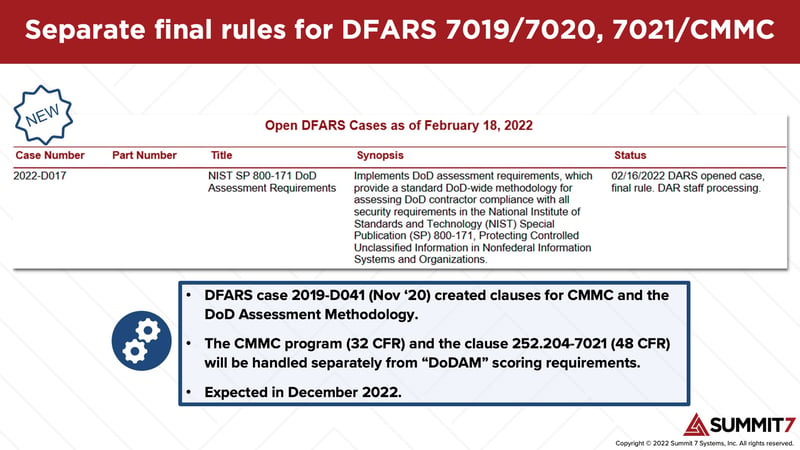
The key concept to keep in mind with DFARS cybersecurity obligations is that CMMC is the overall assessment program for the requirements contained in NIST SP 800-171. Thus, CMMC rulemaking has little to do with the contents of NIST SP 800-171. Instead, CMMC rulemaking will address details of the program such as specific guidance on POAMs, reciprocity, and program schedules.
-
The CMMC rules are currently on the DoD’s rulemaking docket for publication in December of 2022. We anticipate a publication window between December 2022 and May 2023, which fits squarely in DoD’s public estimate of 9 – 24 months.
CMMC
-
A recent DoD CIO Town Hall webinar in February 2022 indicated that CMMC 2.0 Level 2 “bifurcation” would be deprecated and that most of the 80,000 companies who store, process, or transmit CUI in the defense industrial base would be required to undergo an external assessment from a CMMC C3PAO.
-
The primary constraint on the roll-out of the assessment program will be the capacity of the assessment ecosystem. Specifically, the number of C3PAO organizations and the number of certified assessors. As a result, this is a key metric to monitor moving forward. The faster the DoD and the CMMC-AB can expand the assessment ecosystem, the more likely you will be required to schedule an assessment, especially if you are a supplier to large prime contractors like Northrop Grumman, Lockheed Martin, Raytheon, etc.
-
The “provisional” CMMC program is expected to end by Summer 2022. This means that CMMC “provisional” assessors and instructors will be replaced by officially certified assessors and instructors. Much of this change depends on the DoD releasing the official certification exams that correspond with the already released official training curricula.
-
Additionally, the DoD needs to release the CMMC Assessment Process Guide (“CAP”) and provide access to CMMC eMASS for storing assessment artifacts and results.
-
The end of the “provisional” program should closely coincide with the start of an interim period marked by voluntary CMMC assessments. The DoD has indicated that early adopters of voluntary assessments could receive incentives such as certifications that are good for 4-5 years rather than merely 3. Additionally, the DoD has indicated that CMMC certifications will be used as source selection criteria, further incentivizing early adoption.
NIST
-
Remembering that NIST special publications don’t exist in isolation is important. NIST SP 800-171 is a prime example because it is almost entirely derived from the much larger control catalog in NIST SP 800-53. As a result, changes to NIST SP 800-53 and other flagship documents like NIST SP 800-160 are eventually reflected in revisions and updates to NIST SP 800-171.
-
Given the recent changes to NIST SP 800-53 revision 5, combined with the DoD’s desire to plug known holes in the aging NIST SP 800-171 standard, we know that there will be more than 110 controls in the upcoming revision. NIST SP 800-171 revision is expected in late Summer or early Fall 2022.
-
Additionally, CMMC 2.0 Level 3 pertains to the requirements contained in the upcoming NIST SP 800-172, which primarily contains control enhancements to NIST SP 800-171 requirements. As a result, companies with CMMC 2.0 Level 3 certification requirements will have to fully implement all CMMC 2.0 Level 2 requirements.
DHS
-
As explained above, the CUI program applies to all federal agencies and NIST SP 800-171 is the minimum set of security requirements for all categories of CUI. The DoD is only one agency and CMMC is simply the DoD’s attempt to establish an assessment program for their supply chain.
-
DHS has been working on its agency-specific CUI rule since 2017. Look for similar cost estimates, timelines, and pain points in the supply chains of other agencies, compared to what has appeared in the defense industrial base.
-
The key element to watch for is whether DHS will establish a CMMC-like assessment program of their own for the requirements in NIST SP 800-171.
Ultimately, updates to federal policies will have significant impact on the security and compliance posture of suppliers in the Defense Industrial Base. Knowing and preparing for what is ahead will benefit you, your company, and your customers, as there will be a rush for resources, remediation, and service providers as rules are published.





