CMMC Compliance Guide
Understanding the Cybersecurity Maturity Model Certification (CMMC 2.0) for Defense Contractors

Free Resource: CMMC Readiness Brief
Your Blueprint to CMMC Success with Leadership Support
On December 26, 2023, CMMC 2.0 was published. We know this is a stressful time for many government contractors. We've provided a wealth of knowledge below, but if you need to speak with an expert now to get answers, fill out this form and we'll get in touch with you within 1-2 business days.
Key Takeaways:
- CMMC is the Department of Defense's method for ensuring that contractors have implemented adequate cybersecurity measures to protect sensitive data.
- The CMMC 2.0 rule was published on December 23, 2023.
- CMMC assessments will start in Q1 2025.
- The phased rollout of CMMC in contracts will begin in Q3 2025.
- Prime contractors will likely expect subs to be CMMC compliant well before the phased rollout period.
- There are 3 levels of CMMC depending on the types of data you handle as a part of your DoD contracts.
- For Level 2, which is the most common, it takes an average of 12-18 months to prepare for a CMMC assessment PLUS another 9-15 months wait time to get assessed.
- The CMMC rule is built on the assumption that contractors have already implemented NIST SP 800-171.
- If you're in a time crunch, you can do a CMMC Enclave to ensure that your business doesn't lose contracts while you gradually move your company all-in over time.
Sections
Sections
See our CMMC Solutions
Ready to start your CMMC compliance journey? Click below to see how to get started.
What Is CMMC?
CMMC, which stands for Cybersecurity Maturity Model Certification, is the DoD's method for assessing the ability of organizations in the DoD supply chain to protect sensitive data such as FCI, CUI, and/or ITAR. There are three levels of CMMC. We will cover each of these in-depth in the How to Become CMMC Compliant section of this guide.
Many Americans are unaware, but the United States is currently in a Cyber War. And we're losing.
Every day, foreign adversaries attempt to steal information about the advanced technologies that drive our industrial and defensive dominance. The primary target is the U.S. Department of Defense (DoD) and its associated supply chain, known as the Defense Industrial Base (DIB).
The magnitude of the problem is daunting:
- By engaging in Intellectual Property theft, China now leads in 37 out of 44 critical technologies, including areas like Optics, Advanced RF, and Cybersecurity.
- Former NSA Director General Keith Alexander has referred to this cybersecurity crisis and Intellectual Property theft as "the largest transfer of wealth in human history."
Safeguarding sensitive data and Intellectual Property has never been more crucial for DoD contractors in the Defense Industrial Base.
The CMMC program is the DoD's attempt at solving this problem.
CMMC 1.0 to CMMC 2.0
The first iteration of CMMC (CMMC 1.0) was released in September 2020 and made effective on November 30, 2020. In November 2021, CMMC 2.0 was announced as a response to the review of CMMC 1.0.
This video explains what changed from CMMC 1.0 to CMMC 2.0:
Who does CMMC apply to?
CMMC directly impacts organizations supporting the Department of Defense or higher education research institutions handling:
- Federal Contract Information (FCI)
- Controlled Unclassified Information (CUI)
- Covered Defense Information (CDI)
- Controlled Technical Information (CTI)
- or ITAR/export-controlled data
According to the DoD, over 200,000 aerospace and defense suppliers are expected to meet CMMC compliance. Of those 200,000, DoD estimates that over 80,000 will need a CMMC level 2 certification. 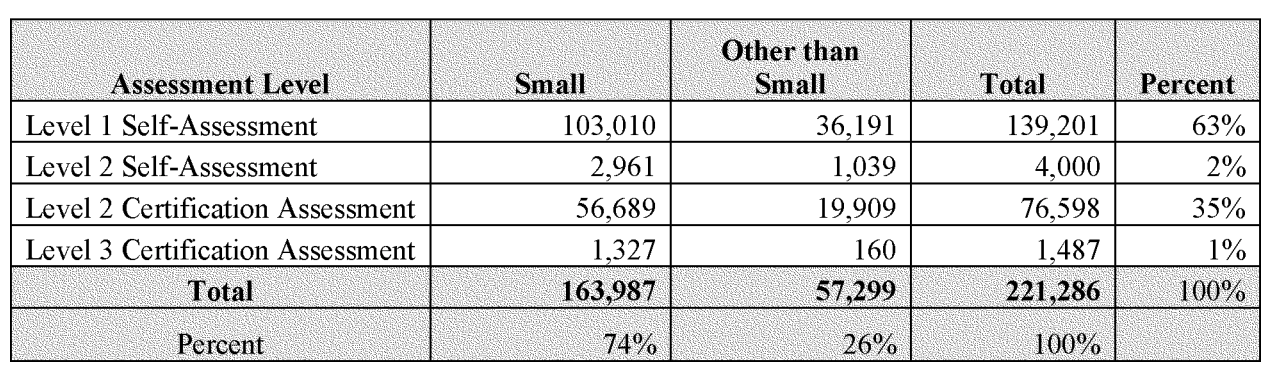
Why should I become CMMC compliant?
CMMC compliance is required if you plan to do business with the Department of Defense.
Aside from that, here are also other advantages. Here are some key benefits of CMMC:
CMMC enhances your cybersecurity and protects the American dream.
By adhering to the framework's controls and practices, businesses significantly reduce their vulnerability to cyber threats and attacks. When American businesses are more secure in the handling of sensitive government information, our country is more secure from enemy attacks.
CMMC creates business opportunities and a competitive edge.
CMMC compliance opens the door to lucrative DoD contracts. As the government prioritizes cybersecurity, businesses that meet these stringent requirements are more likely to secure contracts and partnerships.
With CMMC as a contractual requirement for DoD contracts, companies that attain certification gain a competitive edge in the Defense Industrial Base. Being able to demonstrate a commitment to robust cybersecurity practices can set them apart from non-compliant competitors.
CMMC creates long-term viability and supply chain resilience.
As cybersecurity threats continue to evolve, compliance with CMMC ensures that businesses are better equipped to adapt to new challenges. The CMMC framework promotes an ongoing commitment to security, which is crucial in an ever-changing digital landscape.
Also, by ensuring that suppliers and partners meet the necessary cybersecurity standards, the entire ecosystem becomes more secure.
Safeguarding sensitive data and Intellectual Property has never been more crucial for DoD contractors in the Defense Industrial Base.
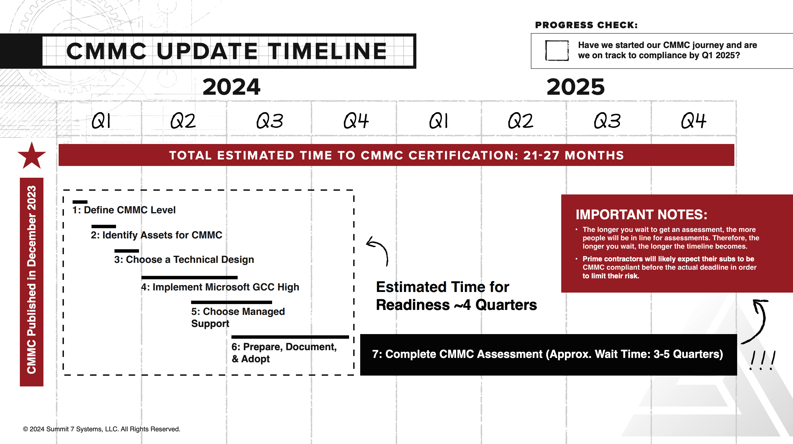
When Will CMMC 2.0 Appear In Contracts?

Here's what you need to know about when CMMC will be in contracts:
- The CMMC rule was published on December 26, 2023.
- It takes an average of 12-18 months to prepare for a CMMC level 2 assessment.
- CMMC assessments will be available in Q1 2025.
- Due to the shortage of CMMC assessors, the approximate wait time for a CMMC assessment is 3-5 quarters (9-15 months).
- The phased roll out of CMMC as a contractual requirement will begin around Q3 of 2025.
- Remember: CMMC checks compliance with DFARS 7012 and other requirements in NIST SP 800-171 that are currently in contracts for DoD contractors handling sensitive information (i.e., the government is assuming these requirements are already met).
For detailed information on the CMMC compliance deadline, refer to our post here.
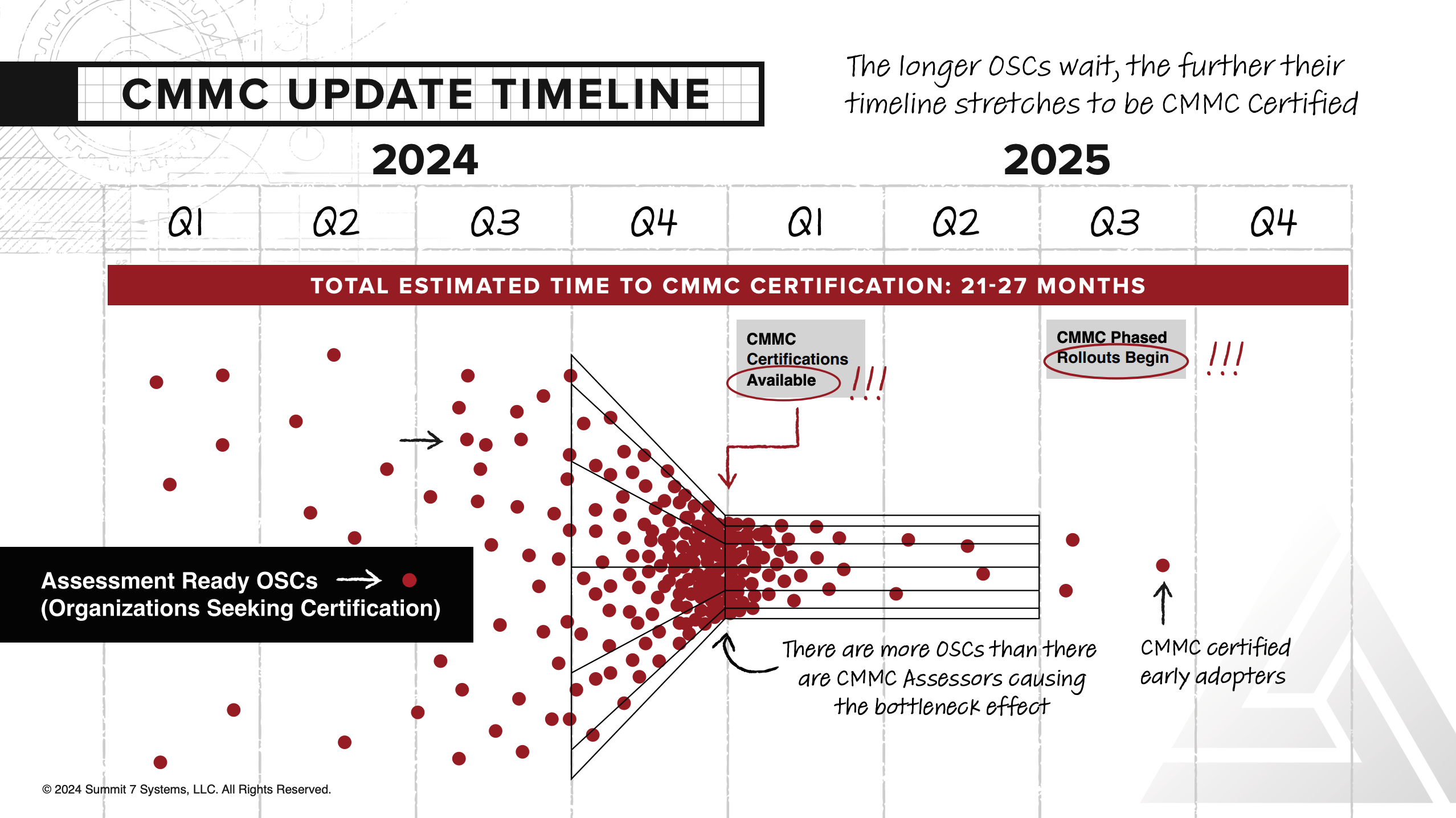
Why not just wait until CMMC phased rollouts begin in 2025?
There are a few reasons to not wait until phased rollouts in contracts begin.
Reason #1 to not wait: Primes will expect it sooner.
Prime contractors' certification requirements flow down to their Subcontractors. Primes will be asking their subs to become CMMC certified as soon as possible to keep their competitive edge.
Here's the question Prime contractors are likely asking themselves:
"Who's more proactively secure and which organization creates less supply chain risk?"
Reason #2 to not wait: The longer you wait, the more of your competitive edge you lose.
According to the CMMC rule, “Organizations Seeking Compliance (OSCs) may elect to complete a self-assessment or pursue a certification assessment at any time after issuance of the rule in an effort to distinguish themselves as competitive for efforts that require an ability to adequately protect CUI.” CMMC compliance will be a significant competitive edge when it comes to bidding on new contracts.
That means your competition will be picking the earliest possible moment to become compliant (Q1 of 2025), trying to edge you out.
Reason #3 to not wait: Waiting puts you further back in the assessment queue.
Lastly, there are more organizations that need CMMC certification than there are CMMC assessors, causing a bottleneck effect. If you wait until the DoD Phased rollout starts in 2025, you will already be behind because of the inevitable backlog.
With these factors in mind, most organizations are looking to Q1 of 2025 to be assessment ready. The question is, will you be ready?
Most organizations underestimate how long becoming assessment-ready will take.
The average time it takes to implement NIST SP 800-171 (12-18 months for a 50-500 person company starting from an average compliance posture) extends beyond the estimated final rule publish date.
So, if you want a shot at staying competitive, your best chance is to start NIST SP 800-171 implementation today.
If you wait, you will be behind your competition.
What You Should Know About the Published CMMC 2.0 Rule
If you're wondering what the key takeaways are from the published CMMC rule, here's what you should know:
The first 150 pages of the rule are basically a summary of "how we got here" and "what to expect".
The crucial details fall in the last 70 pages. This is where you find out all the specifics around what is required for each CMMC level.
- Level 1 is for Federal Contract Information (FCI)
- Level 2 is for Controlled Unclassified Information (CUI). CUI is an umbrella term that includes common data types such as Controlled Technical Information (CTI), and ITAR data.
- Level 3 is for Critical CUI
Since most organizations seeking compliance will be at CMMC Level 2 (roughly 80,000 companies, over a third of the Defense Industrial Base, according to the DoD) we'll focus on takeaways for Level 2.
Key takeaways for CMMC Level 2 include:
- CMMC assesses NIST SP 800-171 Revision 2, not Revision 3.
- All 320 Assessment Objectives in NIST SP 800-171A must be met.
- Once 3rd Party Assessments become available, you need to self-attest to 100% before you can go through a 3rd Party Assessment (C3PAO).
- In order for you to receive a CMMC certification through a Certified 3rd Party Assessment Organization (C3PAO), they will attest that you have fully implemented all 320 assessment objectives.
- Any MSP/MSSP working with the organization must have a Level 2 final certification as well.
- Every year a senior company official must re-affirm that all 320 assessment objectives are still being met.
- Every 3 years a C3PAO must re-certify the organization.
- CMMC is incredibly thorough in assessing NIST SP 800-171 implementation. There are no loopholes.
How Much Does CMMC Cost?
It's very important to understand that CMMC compliance is an investment in the future of your organization. It is NOT a box to check.
CMMC is intended to spark a complete overhaul of the way the American defense supply chain handles sensitive data – so foreign adversaries can't steal the most value assets we have as an international superpower.
That will not and should not be cheap or easy if it's done right.
Having said that, the cost to become CMMC certified will vary a great deal depending on the size and complexity of your organization. However, there are some general costs that you can expect to incur.
When thinking about how to budget for CMMC – there are 5 major buckets to consider:
- Scoping: auditing your systems to locate all of your sensitive data (CUI, ITAR, etc.)
- Licensing: for a CMMC-ready cloud provider like Microsoft Government Cloud
- Implementation: costs associated with implementing CMMC controls
- Migration: moving your current environment into your new, secure cloud provider
- Support: getting the right people/team to meet CMMC's monitoring and threat detection requirements
- Assessment: paying for the actual CMMC assessment (every 3 years)
Total Cost = Scoping + Licensing + Implementation + Migration + Support + Assessment
Each one of these buckets can vary widely depending on your need, organization size, current state of your cybersecurity, etc.
But we can work our way backwards through these budgeting buckets to estimate the cost as best we can without factoring in the details of your organization:
Assessment Costs
As a reminder, these assessment costs are based on the assumption that you have already implemented NIST SP 800-171.
The CMMC rule gives some estimates for how much an assessment could cost and how much support should cost:
For a Level 2 CMMC assessment, the cost will include Assessment Costs (initial and every three years after), and Affirmation Costs (annually). DoD estimates that the cost of assessment and affirmation will be around $104,670.
Remember, that's just the cost of the assessment itself.
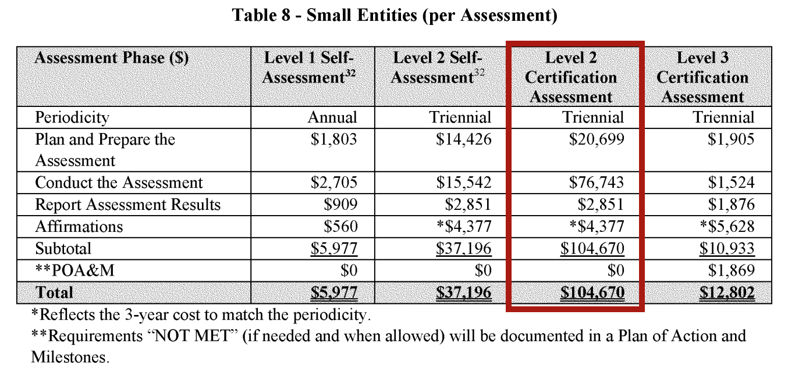
Support Costs
Support costs will include hiring additional staff and/or an External Service Provider (MSP/MSSP) to support your CMMC compliance program on an ongoing basis. To remain CMMC compliant, you'll need active monitoring, threat detection, and incident reporting that will consume a moderate amount of time between your CMMC assessments.
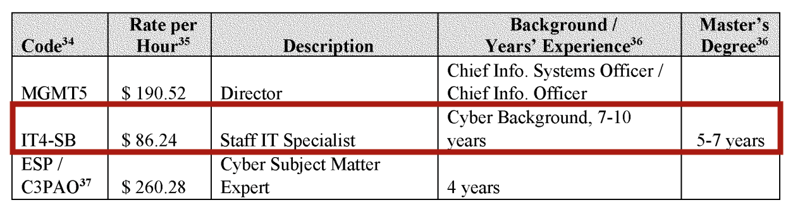
According to DoD, getting an experienced IT professional capable of supporting such an effort would cost somewhere around $86/hour.
Implementation, Migration, and Scoping Costs
If you do actually find a unicorn IT person who also has the bandwidth to support CMMC compliance, you could, in theory, use this person for the implementation, migration, and scoping as well.
Implementation costs will include all the technical changes required to meet the standards that CMMC is intended to check (such as NIST SP 800-171 ) as well as migration to a compliant platform.
Based on the estimated number of hours it could take for a CMMC project, implementation alone could easily consume at least one person's full time job for 12-18 months.
The annual full-time salary of an employee being paid $86.24 per hour would be around $179,000. So keep that in mind when considering first-year implementation, migration, and scoping cost if you were to hire in-house (which you can avoid by outsourcing to a trusted partner).
Licensing Costs
When it comes to licensing, we recommend Microsoft GCC or GCC High. The cost of licensing for your organization is strongly dependent on your approach to CMMC compliance.
Here's why we recommend GCC High:
- Microsoft 365 GCC High is built on Azure Government within dedicated US data centers.
- GCC High is the only Microsoft offering besides the DoD dedicated Microsoft 365 that insures all data resides in U.S. data centers
- GCC High is also supported by background-checked U.S. persons
Those attributes make GCC High suitable for ITAR and EAR data.
Microsoft 365 GCC High is also a suitable cloud platform to house CUI corporately and on behalf of the Government, which requires DISA IL 4 or greater. GCC High is rated at DISA IL 5 and is FedRAMP High equivalent.
If you want a quote, reach out below. Someone from our team will get you the answers you need within one business day:
7 Steps to CMMC Compliance
Aerospace and defense contractors in the Defense Industrial Base looking to achieve CMMC compliance should be taking the following steps:
- Define Your Required CMMC Level
- Identify Assets for CMMC
- Choose a Technical Design For CMMC
- Implement Microsoft Government For CMMC
- Find a Managed Service Provider for CMMC
- Prepare and Document for CMMC
- Complete a CMMC Assessment

Get the Downloadable Version of 7 Steps to CMMC Compliance for free.
Download the CMMC Readiness Brief for Free
Click below to download the CMMC Readiness Brief.